Could you spot a phishing scam if it showed up at your next meetup? Find out how Lainchain’s deception caught professionals by surprise in Paris.
Table of Contents
A crypto trap in Paris
On the evening of Dec. 3, a freelancer meetup took place at Café Oz in Paris, drawing individuals from various industries to network and exchange ideas. Among the attendees was Scott Horlacher, a software engineer and developer.
The evening took an unusual turn with the arrival of two individuals. One was sharply dressed, presenting himself as a lawyer handling the business side of things, while the other, a younger and rugged-looking individual, introduced himself as Leo, a developer. Together, they claimed to represent a new crypto exchange platform called Lainchain.
Horlacher’s discussion with them began innocuously enough. “We were conversing in French,” Scott explained, noting that the developer, who gave the name Leo described Lainchain as a Python Flask app. However, the answers to Scott’s technical questions raised red flags.
“I was questioning him about the settlement layer, like, how are transactions processed and settled on your exchange or platform?”
The Lainchain founder retorted, “you just connect your MetaMask, and you send it directly.” At that point, Horlacher’s suspicions grew. When Horlacher visited Lainchain.com, the problem became evident. “I scrolled over to the sign-up section, and this is then basically when I realized that, oh man, this guy is a scam,” he said.
“The sign-up page has a wallet seed generator directly in it. Clearly, the exchange is managing your private keys, and at any point, it’s a security risk. The person is either really stupid for developing the platform, or they’re a scammer. And I think it’s more likely they are a scammer.”
After confronting the pair about the issue, their confidence unraveled. They left the event shortly after, leaving Horlacher and others to piece together the scam, warning others in attendance.
Determined to get to the bottom of this suspicious encounter, crypto.news partnered with AMLBot, a compliance and blockchain forensics firm. What followed was an in-depth inquiry that exposed Lainchain for what it truly was—a carefully orchestrated phishing scam.
This article unpacks the findings of that investigation and examines how the scam worked, what warning signs to watch for, and, most importantly, how you can protect yourself from falling prey to similar schemes in the future.
Understanding phishing scams and their variations
Before diving deeper into Lainchain’s issue, it’s important to understand the types of phishing scams that exist and how they target victims, particularly in the financial and crypto sectors.
Phishing scams use deception to trick individuals into revealing sensitive information like passwords, seed phrases, or wallet credentials. Unlike direct hacking, phishing relies on social engineering, making victims unwitting participants in their own exploitation.
According to Statista, in 2023, 27.32% of global cyberattacks were financial phishing attacks, down from 36.3% in 2022 and 41.8% in 2021.
Moreover, in 2023, the Federal Bureau of Investigation Internet Crime Complaint Center reported over 69,000 complaints related to financial fraud involving crypto. Estimated losses exceeded $5.6 billion, affecting assets like Bitcoin (BTC), Ethereum (ETH), and Tether (USDT).
Phishing scams often take these forms:
- Email phishing: Generic emails impersonate trusted entities, such as exchanges, prompting users to click malicious links or share login details.
- Spear phishing: Highly targeted scams personalize messages based on specific victims, often impersonating team members or partners to establish trust.
- Clone phishing: Fake websites or apps, such as Lainchain, mimic legitimate ones, tricking users into entering their credentials or connecting wallets.
- Social media phishing: Scammers on platforms like Telegram or Twitter pose as influencers, support staff, or project representatives, enticing victims with fake giveaways or investment offers.
- Malware-based phishing: Malicious apps or links infect devices, capturing sensitive data such as seed phrases, private keys, and credentials.
Phishing in crypto is particularly dangerous because of the irreversible nature of blockchain transactions—once funds are transferred, they cannot be recovered. Understanding these tactics is essential to avoiding them.
Recognizing the warning signs and employing basic security practices, such as two-factor authentication and verifying sources, are crucial steps to protect your digital assets.
How the scam works
According to investigators from AMLBot, Lainchain presented itself as a legitimate crypto exchange but was riddled with fundamental flaws that exposed its true nature. The platform’s interface was far from professional, featuring a rudimentary design that belied its bold claims.
The deception began with a seemingly routine request for users to connect their MetaMask wallets to access the platform’s services. Wallet integration is a common feature in blockchain-based applications, but Lainchain manipulated this process. Instead of a standard authorization prompt, users were asked to input their seed phrases — a practice no legitimate platform would ever endorse, leading to suspicions it was operating as a phishing scam.
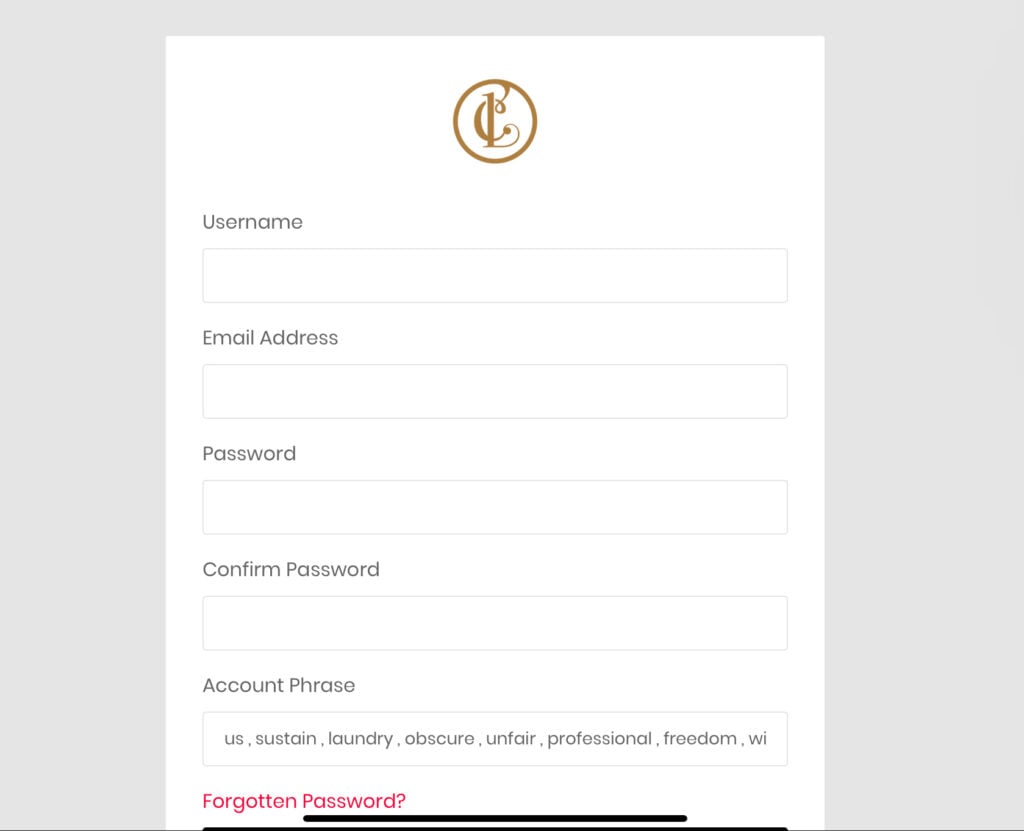
Investigators highlighted that this tactic effectively handed over control of users’ wallets to the scammers. With access to private keys, the perpetrators could freely transfer funds without detection or interference.
Beyond direct theft, Lainchain employed psychological strategies to deepen its exploitation. Victims were lured with promises of extraordinary returns and encouraged to deposit more funds to “unlock maximum potential.”
When users tried to withdraw, they encountered fabricated obstacles like demands for “transaction fees” or “verification charges,” which served only to siphon more money from them.
The investigation also revealed that Lainchain collected personal data during registration, including email addresses and linked wallet details. This information was likely monetized further, sold on dark web marketplaces, and used for phishing campaigns or other forms of identity theft.
Technical investigation findings
Investigators from AMLBot employed Open Source Intelligence techniques to unravel Lainchain’s deceptive operations. A critical breakthrough came from analyzing the domain registration details of lainchain.com.
The domain, registered through HOSTINGER — a low-cost registrar often exploited by scammers — was set up with privacy settings to obscure the owner’s identity.
This deliberate anonymity is a hallmark of cybercriminal operations. Registered on January 30, 2023, and updated on October 30, 2024, the domain’s timeline indicated a prolonged window for defrauding victims.
Further investigation showed that the website was hosted on servers in Helsinki, Finland, under Hetzner Online GmbH, a hosting provider with a reputation for privacy-focused and affordable services. While legitimate, such services frequently attract bad actors looking for cover.
Investigators also found that Lainchain wasn’t an isolated scam but part of a network of fraudulent platforms like Rawkchain and Staxeblock, all built on nearly identical codebases.
Embedded comments in Lainchain’s HTML source explicitly referenced Rawkchain, confirming the sites were clones. This tactic enabled scammers to rebrand and relaunch after exposure, continuing to deceive users.
SSL certificate analysis further linked Lainchain to a suspicious domain, finalsolutions.com.pk, hinting at a broader network for phishing or laundering stolen funds. Moreover, reverse IP lookups and DNS analysis revealed shared servers with other dubious platforms, exposing its reliance on cheap hosting and minimal effort.
Investigators concluded Lainchain exemplified a scalable, low-cost, high-reward scam model, exploiting anonymity and technical shortcuts to prey on users.
Fake identities and social engineering
One of the most alarming aspects of the Lainchain scam was its calculated use of stolen identities and fabricated social proof to build trust and lure victims.
According to investigators, Lainchain’s website prominently displayed images of supposed team members, executives, and founders, complete with impressive titles and professional biographies.
However, investigators revealed that many of these images were stolen from public blockchain events and social media profiles. The scammers repurposed photos of unsuspecting individuals, falsely presenting them as Lainchain’s leadership team.
In one striking example, the image of a well-known Russian politician was used to fabricate an executive’s identity. Other photos traced back to unrelated professionals were paired with fake credentials to further the illusion of credibility.
The deception extended beyond the website. On platforms like Trustpilot, Lainchain showcased numerous glowing reviews, praising its user-friendly interface, robust security, and profitability.
However, further analysis revealed these reviews were fake, originating from newly created or suspicious accounts. Many of these profiles had histories of reviewing other fraudulent platforms, such as Rawkchain and Staxeblock
This combination of stolen identities, fabricated online presence, and glowing but false testimonials created a sophisticated facade, baiting victims into trusting the platform, leaving them vulnerable to financial loss and further exploitation.
Telegram’s privacy and user-friendly features have made it a favored platform for crypto communities — and for scams like Lainchain. Investigators found that Telegram was central to the operation, serving as a hub for promoting the fraudulent platform and connecting with victims.
Scammers operated a private support group where accounts like Arin_lainchain and DanbenSpencer posed as helpful administrators. They shared promotional content and directed users to fake support representatives.
A misstep revealed another key account, Lucifer3971, which investigators linked to black-market activities, including trading stolen data. While other accounts were abandoned, Lucifer3971 remained active, providing critical leads.
Within the group, scammers also created the illusion of legitimacy using fake accounts to simulate activity. These accounts asked questions, shared glowing reviews, and discussed fake withdrawals, making the group appear trustworthy. Moderators welcomed new members with scripted messages and posted fabricated success stories to lure victims further.
The scheme extended beyond Telegram. On Facebook, scammers infiltrated crypto and freelance groups with fake profiles to promote Lainchain. On Twitter, they used bots and fabricated testimonials to amplify their messaging, creating an illusion of credibility and trust.
Data breaches and dark web activity
The Lainchain scam extended its exploitation beyond stealing funds, targeting victims’ personal data to generate additional profit. Investigators uncovered that sensitive information was funneled into large-scale data leaks and sold on dark web marketplaces.
One major repository linked to this network was naz.api, a database notorious for hosting stolen user data from phishing schemes, malware attacks, and browser exploits.
A search of naz.api revealed numerous compromised records tied to Lainchain, including email addresses, phone numbers, passwords, and other private details.
The investigation also identified stealer logs connected to Lainchain. These logs, widely traded on the dark web, provided detailed snapshots of victims’ browser sessions, including saved credentials, autofill data, and screenshots of login portals.
Even more concerning, these logs weren’t isolated—they included data from Lainchain’s predecessor scams, Rawkchainand Staxeblock, feeding into a growing network of stolen information.
Protecting yourself in the crypto space
The Lainchain scam highlights the growing threat of fake platforms designed to mimic legitimate operations, targeting those unfamiliar with crypto systems. While scams like this are exposed, countless others operate undetected, stealing millions from unsuspecting users.
Staying safe starts with understanding how these scams work. Fraudsters often request seed phrases or trick users into connecting their wallets to malicious platforms. Slava Demchuk, CEO of AMLBot, explained the risks:
“By connecting your wallet to an untrusted platform, you may unknowingly grant permissions for malicious smart contracts to access and drain your funds. Before approving any transaction, always review the details carefully. If the platform seems untrustworthy or lacks a proven track record, it’s best to walk away.”
Another common tactic involves fake wallet applications embedded with malware to steal sensitive information. Demchuk stressed to exercise caution when downloading apps:
“Only download applications from reputable sources and verify their credibility by checking user reviews. Keeping your antivirus software up to date adds another layer of protection.”
He also advised a skeptical approach when evaluating platforms:
“Look for red flags like anonymous or unverifiable teams, missing credentials, or inconsistencies in their claims. If anything feels off, pause and do further research. It’s always better to err on the side of caution than risk compromising your assets.”
Reporting scams is equally important. Collaboration among users, developers, and regulators is essential to safeguarding the crypto ecosystem. Staying informed and proactive not only protects individual assets but also strengthens the broader crypto community against these threats.
This article first appeared at crypto.news

