Crypto exchange eXch has denied allegations that it was involved in laundering the funds stolen from Bybit, following claims from several sources.
eXch has denied allegations of laundering funds stolen from Bybit. The initial accusation came from blockchain sleuth ZachXBT on Feb. 22, when he reported in his investigations Telegram group that eXch laundered $35 million of the funds stolen from Bybit. He also noted that 34 Ethereum (ETH) was mistakenly sent to a hot wallet of another exchange during the process.
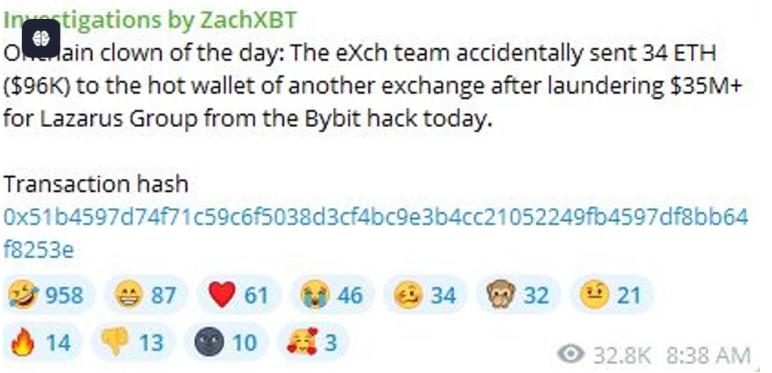
Aligning with ZachXBT’s claims, Nick Bax of the Security Alliance estimated that eXch processed approximately $30 million in transactions tied to North Korea that day.
Similarly, security firm SlowMist stated that a significant portion of Ether had already been converted into Bitcoin, Monero, and other cryptocurrencies through eXch.
⚠️Given the significant amount of ETH already laundered through eXch into BTC, XMR, etc., platforms should tighten risk controls on any funds coming from there.
— MistTrack🕵️ (@MistTrack_io) February 23, 2025
In response, eXch denied the accusations in his Feb. 23 statement on the Bitcointalk forum. However, it did admit to processing a small portion of the stolen assets, which it described as an “isolated incident.” According to eXch, the address […] 1123 received these funds, but no other Ethereum blockchain addresses, aside from deposit addresses, were linked to its platform. It also said that the fees generated from these transactions would be donated for public benefit.
Bybit has been actively working with blockchain forensic experts to trace the stolen funds. It has also offered 10% of the recovered amount as a bounty for assisting in the retrieval process.
The Bybit theft has been attributed to the North Korea’s Lazarus Group, which laundered over $200 million in stolen crypto assets between 2020 and 2023.
According to Elliptic, a blockchain analytics and compliance firm, the Lazarus Group follows a characteristic pattern when laundering the stolen funds.
Specifically, it swaps stolen tokens for native blockchain assets like ETH to prevent token issuers from freezing the funds. In the case of the Bybit hack, stolen tokens were almost immediately exchanged for ETH through decentralized exchanges.
The group then obscured the transaction history by dispersing funds across multiple wallets, moving assets between blockchains, and using mixing services like Tornado Cash. Within two hours of the attack, the stolen funds had been distributed across 50 wallets, each containing approximately 10,000 ETH. By Feb. 23, an estimated 10% of the stolen assets—valued at $140 million—had already been moved.
According to Elliptic, the stolen ETH is now being converted into BTC, a step that precedes further obfuscation through mixers. However, the large volume of assets may complicate this process, Elliptic explained.
This article first appeared at crypto.news

